Secure API Development
Comment security mechanisms for more securre APIs.
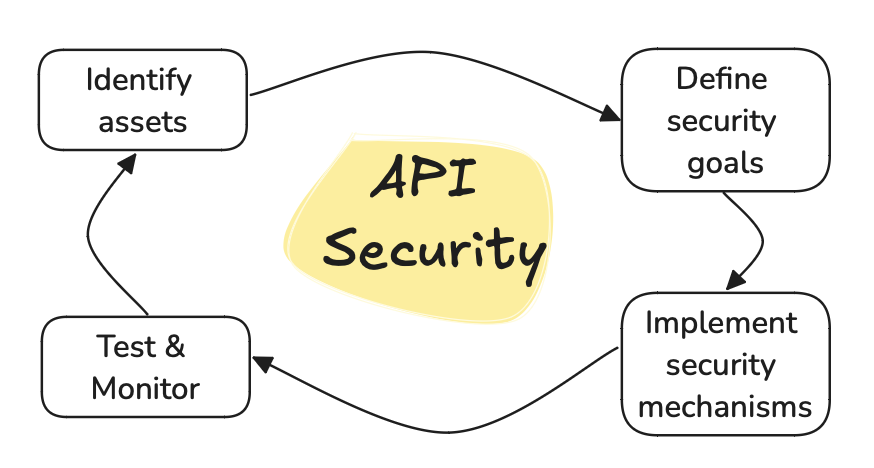
When designing a secure API, various aspects must be considered to safeguard your system against potential threats.
These include identifying the assets that need protection, defining security goals, implementing security mechanisms, and understanding the environment in which the API operates.
This article explores these elements by presenting the most common security mechanisms, the importance of input validation, and the necessity of proper authentication and access control.
Key Security Considerations
Identifying Assets
APIs are often responsible for managing sensitive assets, such as customer information, credit card details, and database contents.
Protecting these assets is crucial, and this protection is achieved by setting clear security goals and employing appropriate mechanisms.
Defining Security Goals
Defining security goals are vital in defining what it means to protect your assets.
The “CIA Triad” is a well-known framework used to establish these goals:
- Confidentiality: Ensures that information is accessible only to the intended audience.
- Integrity: Prevents unauthorized creation, modification, or destruction of information.
- Availability: Ensures that legitimate users can access the API when needed, without being hindered.
Implementing Security Mechanisms
To achieve the defined security goals, various mechanisms can be applied.
Threats are countered by employing these mechanisms, which are tailored to the specific environment in which the API operates.
It is significantly more cost-effective to consider security during the development phase rather than addressing defects post-production.
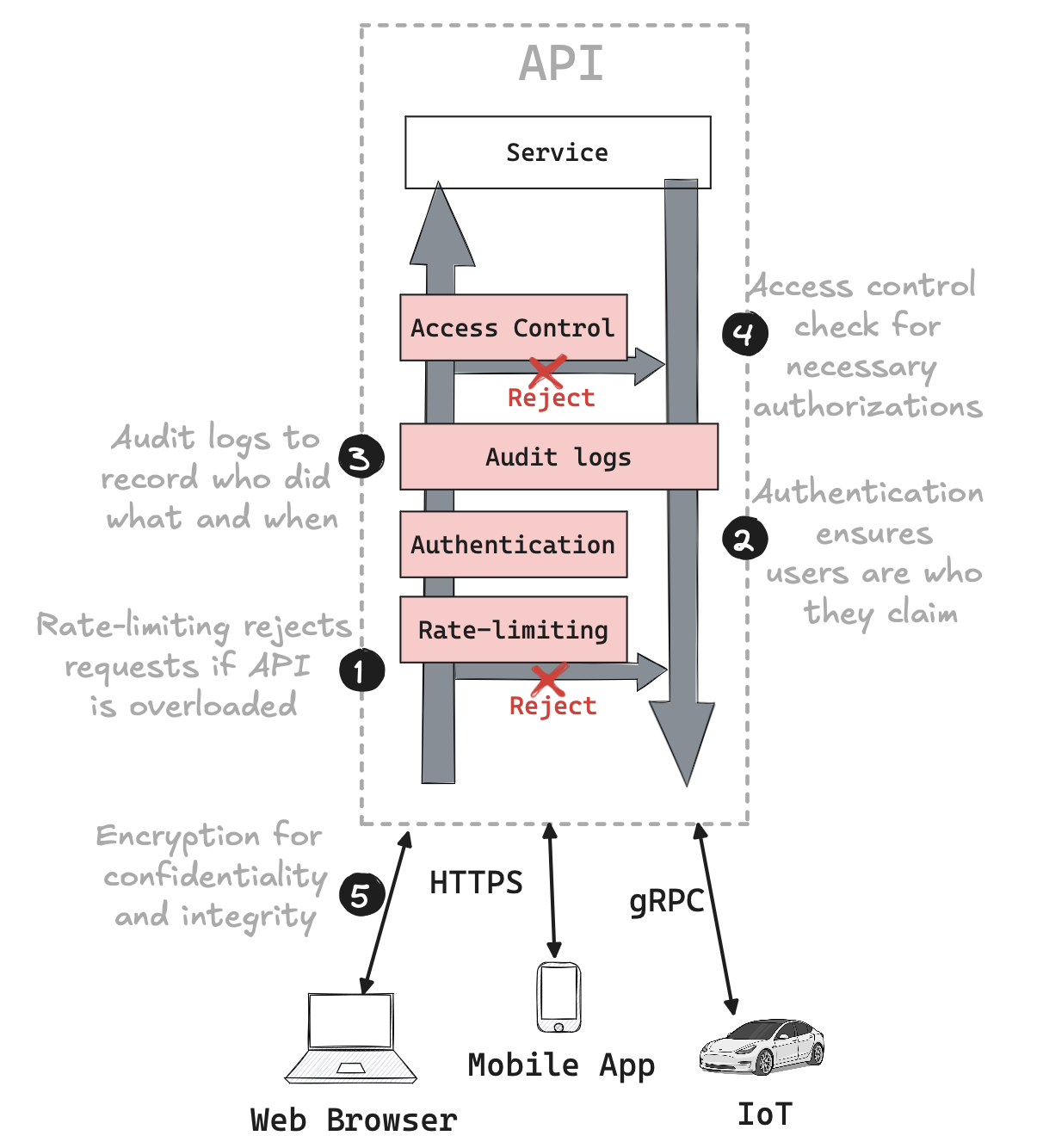
Several security mechanisms are essential for any well-designed API:
- Encryption: Protects data from being read by unauthorized parties, both in transit and at rest. Modern encryption also ensures that data cannot be tampered with by attackers.
- Authentication: Verifies that users and clients are who they claim to be.
- Access Control (Authorization): Ensures that every request to the API is properly authorized.
- Audit Logging: Records all operations to provide accountability and enable proper monitoring.
- Rate-Limiting: Prevents any single user or group from monopolizing resources, ensuring fair access for all legitimate users and ensuring availability.
Developing Secure REST APIs
REST APIs are well-suited for a wide range of applications, particularly in web and cloud-based environments, but also introduce specific security considerations that need to be addressed during development.
This section explores key strategies to protect your APIs from common vulnerabilities, such as injection attacks, improper input validation, and denial of service (DoS) attacks.
Preventing Injection Attacks
Injection attacks remain a significant threat to software security.
They occur when unvalidated user input is incorporated directly into dynamic commands or queries, allowing attackers to control the executed code.
To prevent injection attacks:
- Prepared Statements: Use APIs that support prepared statements, where user inputs are clearly separated from dynamic code. This ensures that the database cannot mistake user input for executable code.
- Permissions: Limit database permissions to prevent unauthorized actions. For example, if your API doesn’t need to delete tables, don’t grant it that permission. This reduces the potential impact of an SQL injection attack.
Input Validation and Safe Output
Security flaws often arise when attackers submit inputs that violate code assumptions. To mitigate this:
- Input Validation: Define acceptable inputs using well-established formats and libraries. An allow list, specifying valid inputs, is more secure than a blocklist, which tries to exclude invalid ones.
- Safe Output: Ensure that all API outputs are well-formed and cannot be exploited. Apply standard HTTP security headers to all responses and double-check error responses.
Rate-Limiting for Availability
Rate-limiting is crucial in defending against denial of service (DoS) attacks. By applying rate limits to all requests, especially unauthenticated ones, you prevent your servers from being overwhelmed by excessive traffic.
This should be the first security measure applied when processing a request.
Authentication to Prevent Spoofing
Authentication is vital for knowing who is performing an operation in your API.
While rate-limiting applies to all requests, authentication ensures that subsequent security controls, like audit logging and access control, function correctly.
HTTP Basic authentication, a widely used method, involves sending credentials in a standard HTTP header.
Web browsers have built-in support for HTTP Basic authentication as does curl and many other command-line tools.
This allows you to send a username and password to the API, but you need to securely store and validate that password.
A better way would be to outsource authentication to another organization using a federation protocol like SAML or OpenID Connect or by using an LDAP (Lightweight Directory Access Protocol) directory.
Using HTTPS
Encryption via HTTPS is essential for protecting data transmitted between the client and API.
HTTPS ensures that the server presenting the API is legitimate by verifying its certificate.
Without HTTPS, sensitive data like passwords could be intercepted by malicious entities.
Audit Logging for Accountability
To maintain accountability, all actions performed using your API should be recorded in an audit log.
These logs should be sent to a centralized Security Information and Event Management (SIEM) system for analysis, helping detect potential threats and unusual behavior.
Implementing Access Control
Beyond basic authentication, access control determines what actions a user can perform.
An access control list (ACL) specifies which users can access specific objects and defines the permissions for each user.
Avoiding Privilege Escalation
Privilege escalation attacks can be mitigated by restricting the ability to grant permissions.
Ensure that new users are not granted more permissions than the existing user who is adding them, or restrict permission-granting capabilities to users with full permissions.
Securing gRPC APIs
gRPC is an open source Remote Procedure Call(RPC) framework that can be used to build scalable and robust applications.
gRPC APIs, unlike REST APIs, use a binary protocol (Protocol Buffers) instead of JSON and are designed for high-performance communication between services, often in microservices architectures.
To develop secure gRPC APIs, consider the following recommendations:
- Use Mutual TLS (mTLS): Ensure secure communication by implementing mTLS, which not only encrypts data in transit but also authenticates both the client and the server.
- Use Streaming Carefully: If using gRPC’s streaming capabilities, ensure proper handling of stream flow and limits to avoid resource exhaustion and ensure secure data handling.
- Control Service Exposure: Only expose necessary gRPC services and methods, and ensure that internal services are not accidentally exposed to external clients.
- Enable Logging and Monitoring: Implement comprehensive logging and monitoring to track access patterns, detect anomalies, and facilitate auditing of gRPC calls.
Other controls from the REST APIs mitigations are still valid for gRPC APIs. This includes enforcing authentication and authorization, validating inputs and outputs, rate-limiting as well as secure handling of errors.
Conclusion
API security is a multifaceted challenge that requires careful consideration of assets, security goals, and appropriate mechanisms.
By focusing on input validation, rate-limiting, authentication, and access control, developers can create robust APIs that resist common threats and protect valuable assets.