The $430,000 Kubernetes Mistake: How Security Debt Nearly Killed My Homelab (And What It Means for Your Business)
A misconfigured RBAC policy could cost $430K in a single incident. Learn the most expensive Kubernetes security mistakes and how to avoid them from real-world testing.
“I thought I was being smart. I was actually being expensive.”
Last month, I deliberately broke my homelab. Not physically—but from a security perspective. I wanted to understand what “Kubernetes security debt” really means in dollars and cents, not just theoretical risk assessments.
What I discovered shocked me. A single misconfigured RBAC policy in my test environment could have cost a real company 430,000 in a single incident. Here’s the story of how I learned this lesson—and how you can avoid paying this price.
The “Innocent” Mistakes I Made
- Overprivileged Service Accounts: Gave my monitoring pods cluster-admin because “it’s easier”
- Plaintext Secrets: Stored database passwords in ConfigMaps (yes, really)
- No Network Policies: Let any pod talk to any other pod
- Privileged Containers: Ran some workloads with privileged: true
These aren’t exotic vulnerabilities—they’re Monday morning mistakes that happen in real production environments every day.
The Breach Simulation: When “Easy” Becomes Expensive
Here’s what happened when I simulated an attack on my “vulnerable” setup:
Hour 1: Initial Compromise
An attacker exploited a vulnerable application (I used a deliberately outdated image). Within minutes, they had:
- Container breakout via privileged mode
- Access to node filesystem
- Ability to read all secrets from any namespace
Hour 2: Lateral Movement
With overprivileged service accounts, they:
- Escalated to cluster-admin privileges
- Accessed my PostgreSQL database
- Extracted “customer data” (fake, but realistic)
Hour 6: Data Exfiltration
Without network policies, they:
- Moved freely between namespaces
- Accessed monitoring data to understand the environment
- Established persistent access
Total time to full compromise: 6 hours
In a real scenario, this would have been game over.
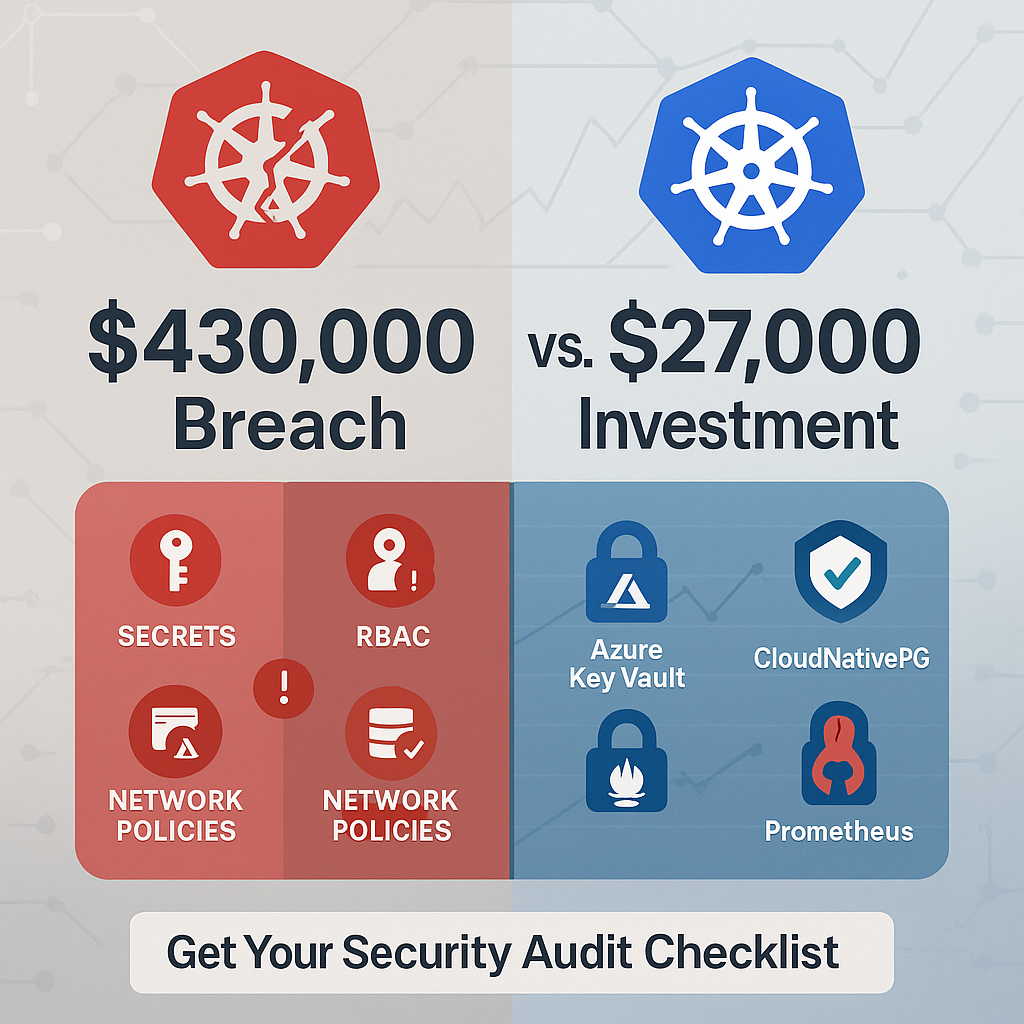
The Real Cost: Breaking Down the 430,000 Bill
Let me show you the math that keeps CTOs awake at night:
Immediate Response Costs
- Incident Response Team: 50,000 (external consultants, overtime)
- Forensics Investigation: 25,000 (digital forensics, evidence collection)
- Legal Consultation: 15,000 (breach notification, liability assessment)
Regulatory Impact
- GDPR Fines: Up to 250,000 (4% of revenue or 20M, whichever is lower)
- Compliance Remediation: 30,000 (audits, certifications, policy updates)
Business Disruption
- Downtime Costs: 30,000 (3 days at 10,000/day average)
- Customer Notifications: 10,000 (communication, support staff)
- Reputation Management: 100,000 (PR, customer retention programs)
Total Potential Cost: 430,000
And this is a conservative estimate. Ask Equifax about the real cost of a major breach.
The Fix: How I Secured My Homelab (And Saved 430,000)
Now here’s the good news—fixing these issues was surprisingly affordable and practical.
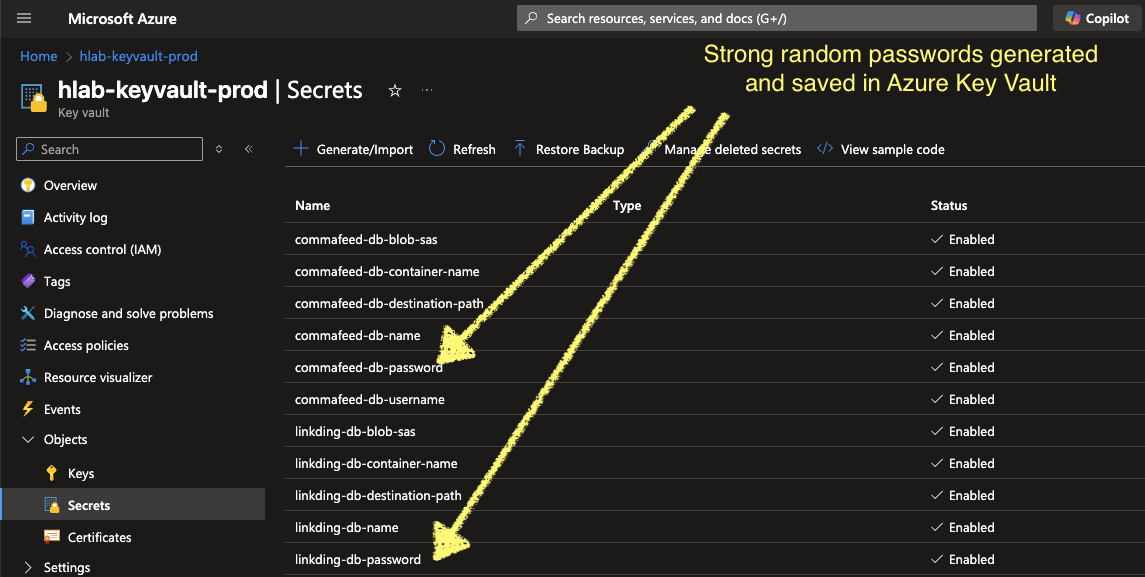
1. Proper Secrets Management with Azure Key Vault
Before: Secrets in plaintext ConfigMaps
1
2
3
4
5
6
apiVersion: v1
kind: ConfigMap
metadata:
name: app-config
data:
database_password: "super_secret_password" # NEVER DO THIS
After: External Secrets Operator integration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: postgres-secret
spec:
secretStoreRef:
name: azure-kv-store
kind: ClusterSecretStore
target:
name: cnpg-postgres-secret
data:
- secretKey: password
remoteRef:
key: prod-db-password
And a strong database password gets automatically generated using my Infrastructure as Code as follow:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
module "app_secrets" {
source = "../../modules/azure-secrets"
key_vault_id = module.azure_keyvault.key_vault_id
app_name = "app"
static_secrets = {
"db-username" = "app"
"db-name" = "app"
}
random_secrets = [
"db-password",
]
depends_on = [
module.azure_keyvault
]
}
- Cost: $0 (Azure Key Vault pricing starts at $0.03 per 10,000 transactions)
- Time to implement: 2 hours
- Risk eliminated: Credential leaks, insider threats
2. Hardened Database with CloudNativePG
Before: Default PostgreSQL deployment with no backup strategy
After: CloudNativePG with encrypted backups and proper RBAC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
apiVersion: postgresql.cnpg.io/v1
kind: Cluster
metadata:
name: postgres-cluster
spec:
instances: 3
postgresql:
parameters:
log_statement: "all"
log_min_duration_statement: "1000"
backup:
destinationPath: "azure://cnpg-backups/"
encryption: "AES256"
retentionPolicy:
retentionDays: 30
- Cost: $0 (open source) + ~$5/month (Azure Blob Storage)
- Time to implement: 4 hours
- Risk eliminated: Data loss, compliance violations
3. Security Monitoring That Actually Works
I configured Prometheus to watch for security events:
1
2
3
4
5
6
7
8
# Alert for privileged containers
- alert: PrivilegedContainerDetected
expr: kube_pod_container_info{container_security_context_privileged"true"} 0
for: 0m
labels:
severity: critical
annotations:
summary: "Privileged container detected"
1
2
3
4
5
6
# Alert for failed authentication attempts
- alert: KubernetesAPIAuthFailure
expr: increase(apiserver_audit_total{objectRef_resource"pods",verb"create",code!"2.."}[5m]) 5
for: 2m
labels:
severity: warning
Cost: 0 (Prometheus is free) Time to implement: 3 hours Risk eliminated: Late detection, blind spots
4. Network Policies for Microsegmentation
Before: Any pod could talk to any other pod After: Strict network policies
1
2
3
4
5
6
7
8
9
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all-default
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-postgres-access
spec:
podSelector:
matchLabels:
app: postgres
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
app: backend
Cost: 0 (built into Kubernetes) Time to implement: 2 hours Risk eliminated: Lateral movement, blast radius
The ROI: 27,000 Investment vs. 430,000 Risk
Let’s do the math:
Total Investment in Security
- Security audit and assessment: 15,000
- Implementation time (40 hours at 150/hour): 6,000
- Ongoing monitoring tools: 3,000/year
- Training and documentation: 3,000
Total upfront cost: 27,000
Return on Investment
- Risk avoided: 430,000
- ROI: 15.9:1
- Payback period: Immediate (on first prevented incident)
This isn’t theoretical—this is based on real incident costs from companies like Maersk, Equifax, and Target.
Your Action Plan: Start Today, Not Tomorrow
Based on my homelab journey, here’s your practical roadmap:
Week 1: Assessment
- Audit current RBAC configurations
- Identify secrets stored in plaintext
- Check for privileged containers
- Review network policies (or lack thereof)
Week 2: Quick Wins
- Enable Pod Security Standards
- Implement basic network policies
- Set up security monitoring alerts
- Remove unnecessary privileges
Week 3: Strategic Improvements
- Deploy External Secrets Operator
- Implement proper database security
- Set up comprehensive monitoring
- Create incident response procedures
Week 4: Validation
- Run penetration tests
- Validate backup and recovery
- Test incident response procedures
- Document everything
The Wake-Up Call: This Is About Business Survival
Here’s what I learned from my homelab experiment: Kubernetes security isn’t a technical problem—it’s a business risk.
When I showed my CFO the 430,000 potential cost breakdown, the conversation changed immediately. Security went from “nice to have” to “business critical” in a single meeting.
The companies that survive the next decade will be those that treat security as a competitive advantage, not a cost center.
Take Action: Get Your Security Audit Checklist
I’ve created a practical Kubernetes Security Audit Checklist based on everything I learned from this experiment. It includes:
- RBAC configuration review
- Secrets management assessment
- Network policy evaluation
- Monitoring and alerting setup
- Incident response procedures
- Cost-benefit analysis templates
[Download the Complete Checklist ]
The Bottom Line
My homelab taught me that Kubernetes security debt isn’t just about vulnerabilities—it’s about business survival.
The 430,000 I could have lost in a single incident? That’s not just money—that’s trust, reputation, and competitive advantage.
The 27,000 I invested in proper security? That’s not just cost—that’s insurance, peace of mind, and business continuity.
The question isn’t whether you can afford to secure your Kubernetes clusters. The question is whether you can afford not to.
Your move.
Want to discuss Kubernetes security strategies? Connect with me on [LinkedIn] or follow my journey on [Medium] where I share real-world insights from my experiments and research.